Exposed Personal Information In Manila's Covid-19 Vaccine Website
I am Fernando Nicolei Esperida from Tondo Manila and a college undergraduate 2nd-year student from Colegio de San Juan de Letran taking Bachelor of Science in Information and Technology and as a concerned resident, I noticed a security vulnerability while I was registering my brother to https://www.manilacovid19vaccine.ph from my account.
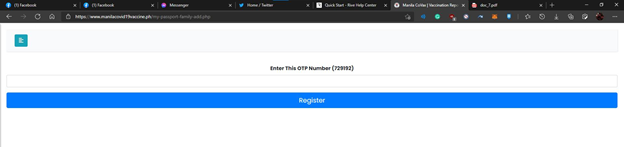
After I added my brother’s information, I noticed that the OTP is only showed on the website and not sent via SMS and that caught my attention to find any security vulnerabilities on the website.
Endpoints
This /search-otp-ajax.php endpoint needs a Mobile Number and First Name for its query and once it is filled up it will send a One-Time Password if the mobile number and first name are correct and registered.
- https://www.manilacovid19vaccine.ph/search-otp-ajax.php?MobileNo=[REDACTED]&FirstName=[REDACTED]
If you try to access this endpoint you will see user information in plain text. This piece of information is being delimited by a '!' character and if we are going to read this information consists of 'OTP!RegistrationID!ReferenceID!'. The Registration ID and Reference ID are important to grab user information from the website as long as the attacker successfully exploited this endpoint.
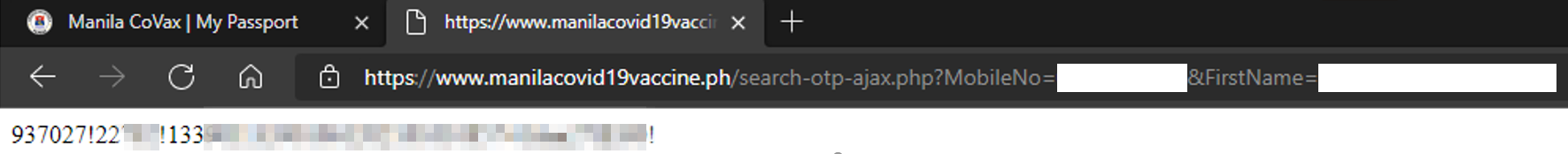
This /search-registration-ajax.php endpoint needs a Registration ID and Reference ID to complete the authentication process. This endpoint just saves authentication information to the browser so the user can reload the browser and still logged in.
- https://www.manilacovid19vaccine.ph/search-registration-ajax.php?RegistrationID=[REDACTED]&ReferenceID=[REDACTED]
These 2 endpoints I found for Vaccination ID and Waiver do not require any additional authorization to access and only need a Registration ID and Reference ID. These endpoints contain a PDF File for a waiver which contains the name, address, and age of the user, meanwhile the vaccination-id contains name, birthday, barangay, and date of registration but no vaccine information even the user is already vaccinated.
- https://www.manilacovid19vaccine.ph/waiver.php?RegistrationID=[REDACTED]&ReferenceID=[REDACTED]
- https://www.manilacovid19vaccine.ph/vaccination-id.php?RegistrationID=[REDACTED]&ReferenceID=[REDACTED]
These 4 endpoints I also found for Vaccination ID and Waiver which do not require any additional authorization to access and only need a Registration ID and Reference ID but it verifies if there is an account that already logged in. Once the attacker has a login session they can now exploit these endpoints.
- https://www.manilacovid19vaccine.ph/my-passport-vaccination-id.php?RegistrationID=[REDACTED]&ReferenceID=[REDACTED]
- https://www.manilacovid19vaccine.ph/my-passport-vaccination-id-back.php?RegistrationID=[REDACTED]&ReferenceID=[REDACTED]
- https://www.manilacovid19vaccine.ph/my-passport-family-members-vaccination-id.php?RegistrationID=[REDACTED]&ReferenceID=[REDACTED]
- https://www.manilacovid19vaccine.ph/my-passport-family-members-waiver-registration.php?RegistrationID=[REDACTED]&ReferenceID=[REDACTED]
This endpoint for Vaccine Certificate only relies on authentication given by search-registration-ajax.php which can be easily triggered if the attacker already used the /search-registration-ajax.php endpoint.
- https://www.manilacovid19vaccine.ph/my-passport-certificate-print.php
Impact
This security vulnerability in manilacovid19vaccine.ph could allow a malicious user or attacker to harvest useful user data from the website like Full Name, Birthday, and Address without having a One-Time Password from the registered mobile number.
An attacker can create a simple script and first uses the search-otp-ajax.php and fill the Mobile Number and First Name field based on the data breaches on our local websites and get the Registration ID and Reference ID to scrape the vaccination id and waiver file. And this could lead to a data breach and a violation of Republic Act 10173 or the Data Privacy Act of 2012.
The attacker can brute force attack the /search-otp-ajax.php using the other local data leaks to gather the Registration ID and Reference ID.

As shown above, it demonstrates how a malicious user can easily take advantage of the security vulnerability in this first data gathering method once the attacker successfully harvests the Registration ID and Reference ID the attacker can now just use the /waiver.php and /vaccination-id.php to harvest the user data.
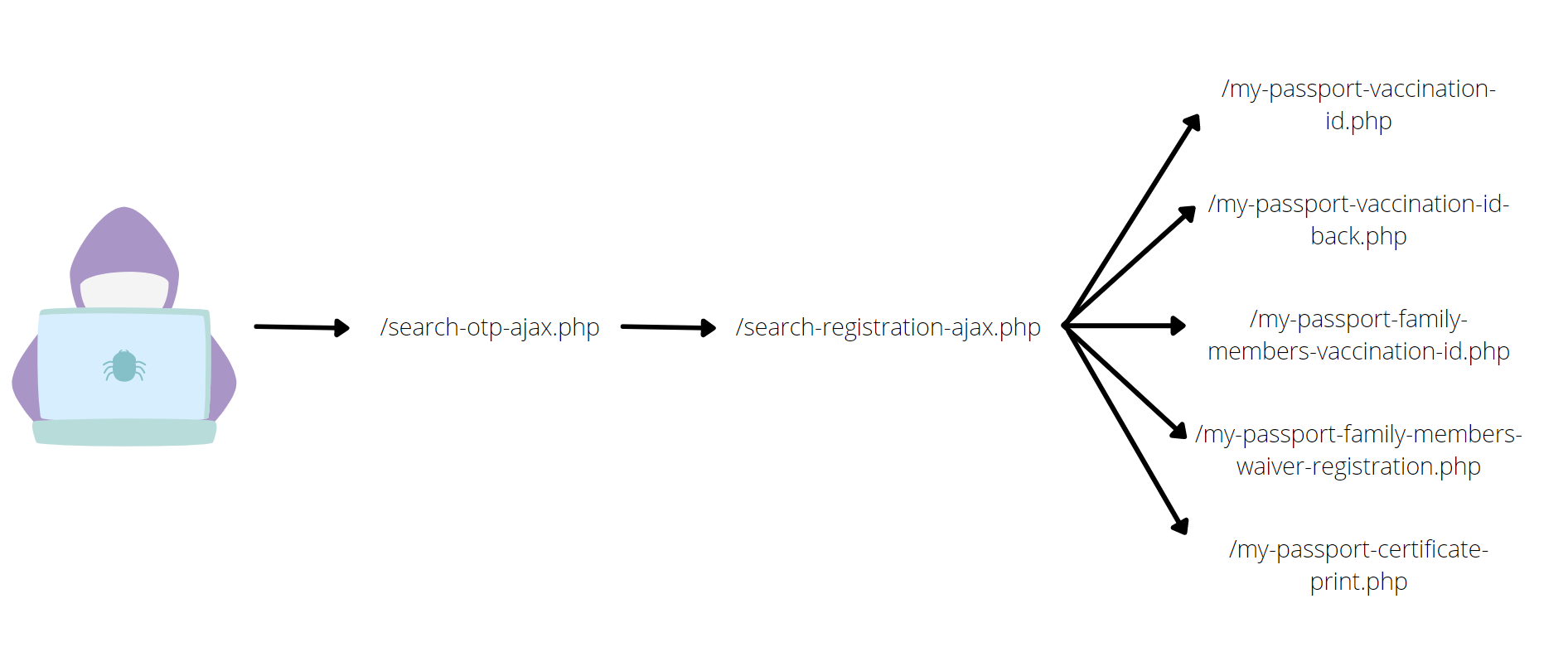
As shown above, This second data gathering method requires a login session and once the attacker successfully harvests the Registration ID and Reference ID the attacker can now use the /search-registration-ajax.php to store a login session and to fool the system that there is already logged in account and the attacker can now use the /my-passport-vaccination-id.php, /my-passport-vaccination-id-back.php, /my-passport-family-members-vaccination-id.php, /my-passport-family-members-waiver-registration.php and /my-passport-certificate-print.php to harvest the user data.
The attacker can harvest the Vaccination ID, Vaccination Certificate, and Vaccination Waiver using only the Registration ID and Reference ID they gathered.
Demo
Solution
The website has a Client-Side Verification in OTP, and this should be done on the Server-Side and the website only receives an authorization token. Currently, the OTP has no other use than moving you to the home page when you entered a valid OTP. They encrypted the plain text OTP from the form field code.
The website code should not contain any user credentials like Registration ID and Reference ID in plain text and this should be encrypted and also this user information should be hidden and not inside of the code. Cookies can be useful to store this kind of encrypted user credentials.
To strengthen the security of those endpoints and avoid data leakage, the security team should add authorization and validation on each request.
Demo Application
This application takes advantage of the vulnerabilities found on the website to download all the available data for the user.
Application Releases: https://github.com/haliknihudas666/hudas-manilacovid19vaccine-downloader/releases/latest
Source Code: https://github.com/haliknihudas666/hudas-manilacovid19vaccine-downloader
Demo Website
This website is connected to an API that processes the request and forwards the response to the website which is bundled in zip archive with the content of all user details.
Website: https://nicolei.games/mnlcovax-download
API: https://mnlcovax.nicolei.games/api/getdata?mobile_number=XXXXXXXXXXX&first_name=XXXXXX
Source Code: haliknihudas666/hudas-manilacovid19vaccine-api (github.com)
Note: OWASP Vulnerability Disclosure was followed.
Featured in
Philstar - Manila City COVID-19 vaccination website vulnerable to data breach, a resident warns | Philstar.com
Timeline
- June 21, 2021 - Report Submitted to Mayor Francisco Moreno Domagoso.
- June 26, 2021 - Sent a Follow-Up email to Mayor Francisco Moreno Domagoso.
- June 27, 2021 - Revisited the website and they fixed the OTP issue on the login.
- June 30, 2021 - Resent a Follow-Up email to Mayor Francisco Moreno Domagoso.
- July 5, 2021 - Vulnerability Report sent to DICT-NCERT
- July 14, 2021 - Resent a Follow-Up email to Mayor Francisco Moreno Domagoso and DICT-NCERT
- July 14, 2021 - DICT-NCERT Responded to email.
- July 22, 2021 - Philstar Published an Article about the Vulnerability
- August 2, 2021 - Updated the blog for newly found vulnerability in Vaccine Certificate and Vaccine ID Back
- August 2, 2021 - Report Submitted to National Privacy Commission
- August 2, 2021 - National Privacy Commission responded to the email.
- September 2, 2021 - Sent a request for feedback to National Privacy Commission
- October 1, 2021 - Posted Publicly
- January 16, 2022 - Posted the application that takes advantage of this exploit